The Assured Satellite Hacking CTF Challenge at Security Fest 2025

Assured proudly sponsored the CTF village at Security Fest 2025 including our jointly organized and hosted Satellite Challenge.
The idea was to inspire participants to explore radio signal hacking and satellite communications, a fascinating domain in terms of security testing and research.
This writeup covers the challenge setup, how it worked, and some of the solutions participants found.

The Challenge Setup
Participants found the challenge instructions on the Security Fest CTF site:
SFSAT-01 - your information provider in space. Downlink frequency 433.500 MHz. This challenge can only be completed locally at the venue, go to the CTF room. Note! Flag does not follow the ctf flag format. Flag consists of two words. Example, "JUPITER PROBE". A special prize awaits the one who solves the most satellite challenges (first). Visit the Assured booth to borrow an RTL-SDR kit.
A downloadable file was also provided, named tle/SFSATS.txt.
Decoding the Clues
The instructions hinted that solving the challenge required:
- A software-defined radio (SDR)
- Knowledge of the satellites' transmission frequency
- The provided TLE (Two-Line Element) data for orbital tracking
The TLE data could be imported into Gpredict to visualize satellite passes.
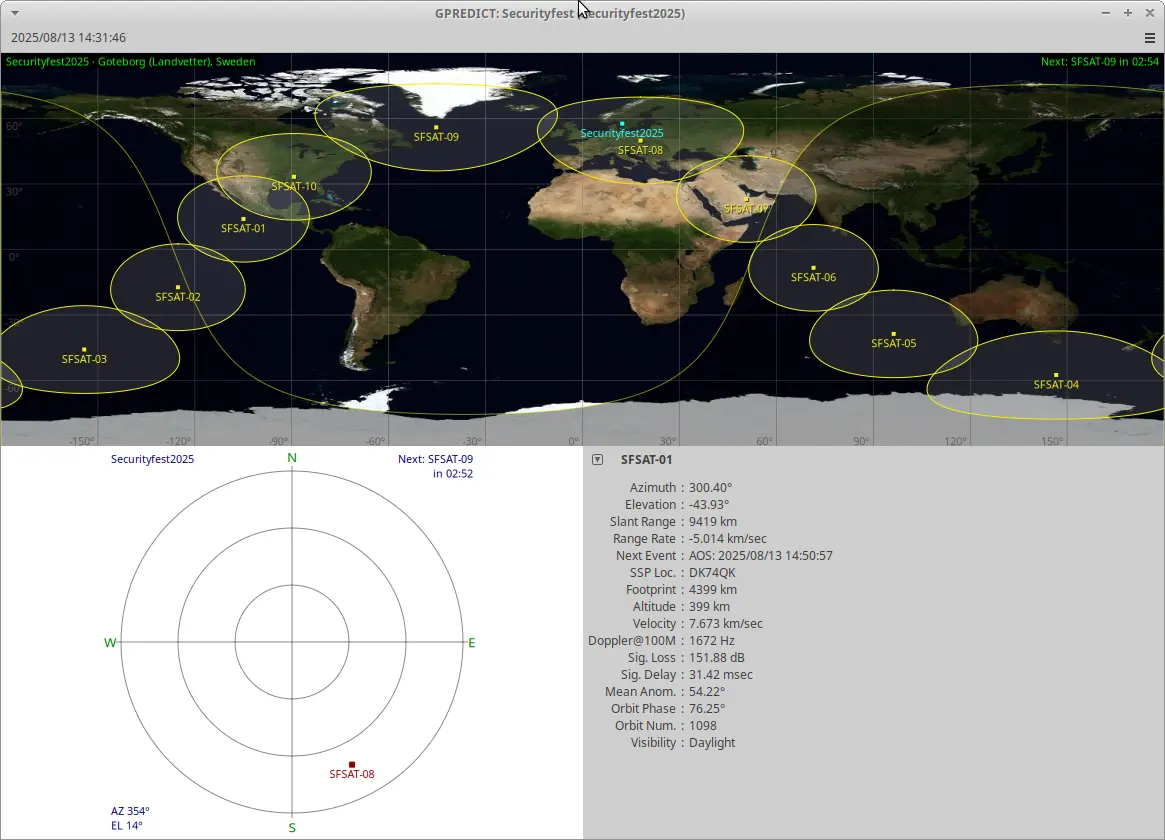
Gpredict revealed that the challenge satellites were in Low Earth Polar Orbit.
This introduces unique challenges for listeners:
- Short reception windows: only ~10-15 minutes per pass
- Long wait times: at least ~90 minutes between passes of the same satellite
To make the challenge solvable during the conference, the satellites were scheduled to pass in sequence several times during the first afternoon. The “satellites” in this challenge were simulated - transmissions were simply turned on/off based on the TLE data, with paths programmed to pass directly overhead.
Antenna Setup and Frequencies
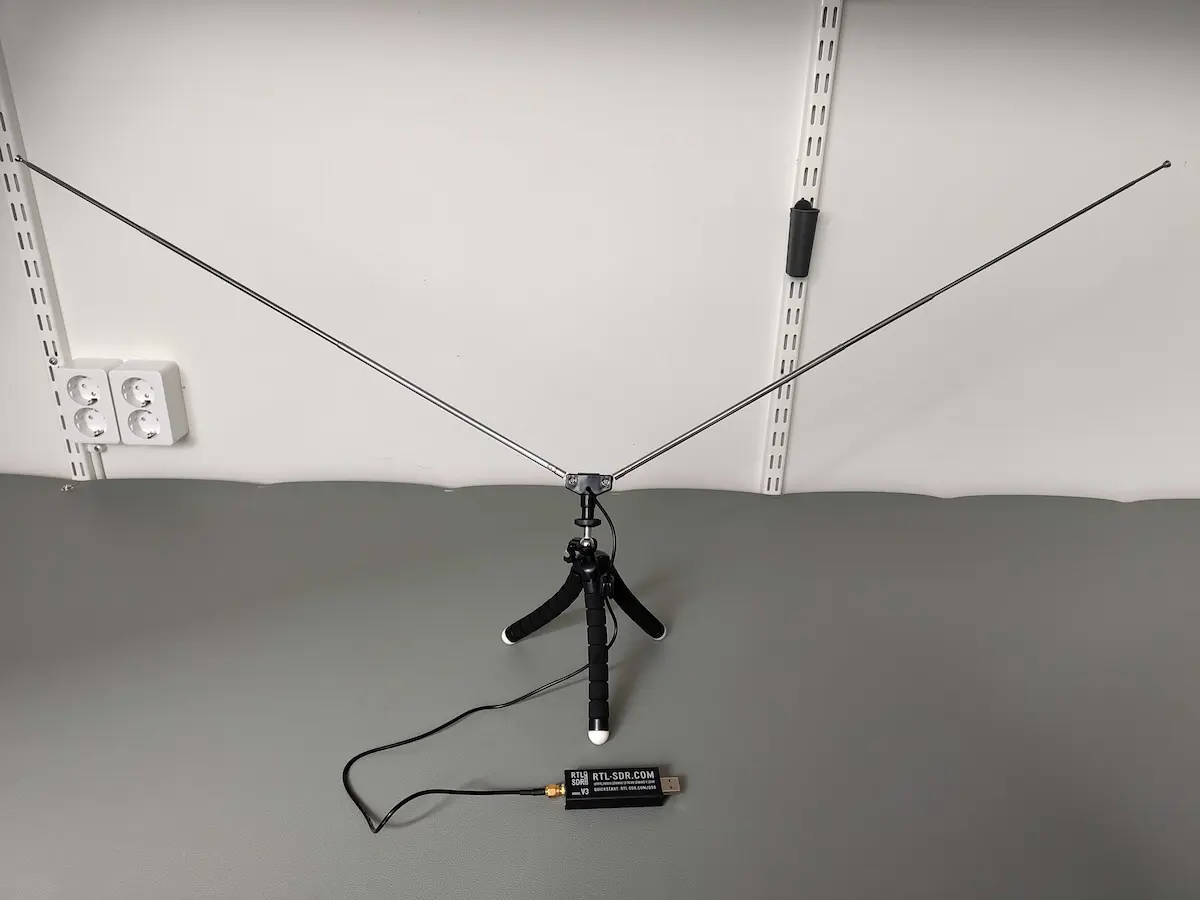
In real life, listening to satellites like NOAA's weather satellites at 137 MHz (APT analogue image transmission) often involves a V-dipole antenna with 53.4 cm elements set at a 120° angle. See image below for a typical setup.
For the Security Fest challenge, things were simplified:
- Frequency: 433.5 MHz
- Location: CTF room
- Antenna: Shorter, non-V dipole possible due to higher frequency and close range
Signal Formats and Strategy
Each “satellite” transmitted a different signal format containing a two-word CTF flag.
Only the first 8 of the 10 listed satellites were actually transmitting.
No hints on signal encoding were provided, participants had to:
- Tune antenna and SDR settings
- Identify the modulation or encoding type during the short pass window
A smart tactic noted by several participants was to record raw IQ data during the pass and process it later without time pressure.
Tools of the Trade
Several open-source SDR software tools could be used for decoding and visualization.
One of the most popular is GQRX. GQRX supports most SDR hardware, offers fine-tuned frequency control, and provides waterfall plots for signal visualization which is perfect for this challenge.
Examples from the Challenge
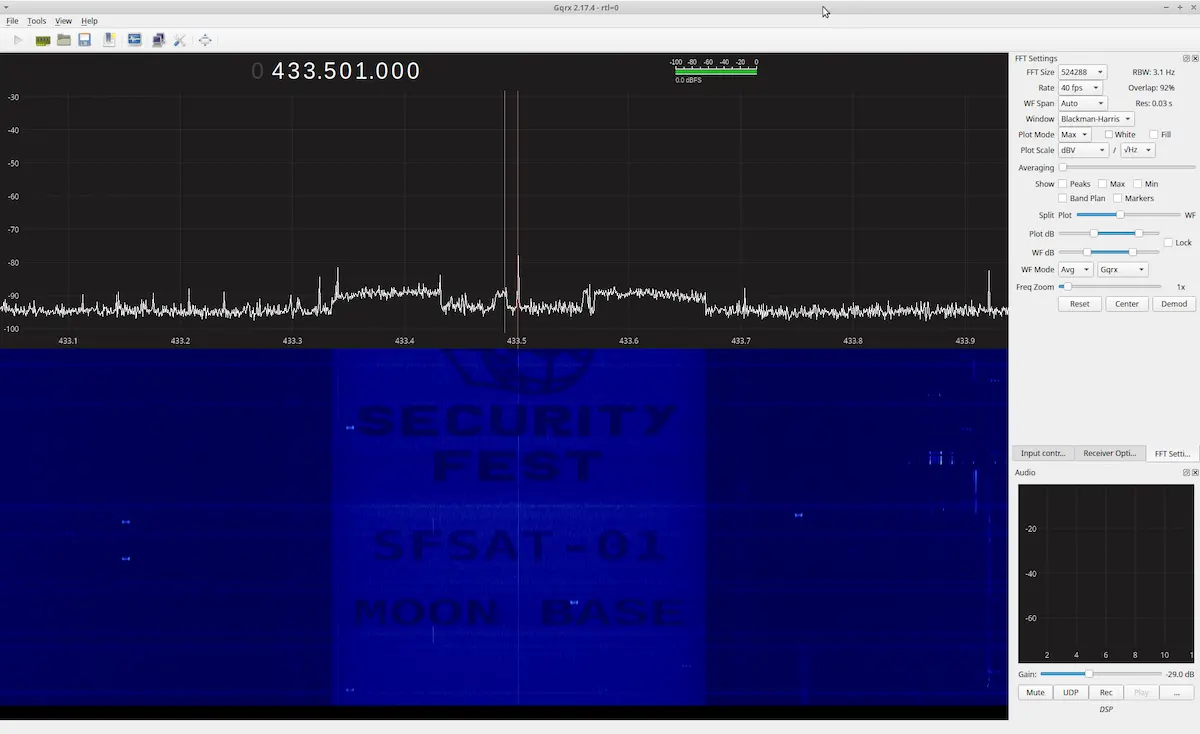
SATF-01 - Spectrum Painting
The first satellite's flag appeared as an image in the waterfall plot, a visual form of transmission known as spectrum painting.
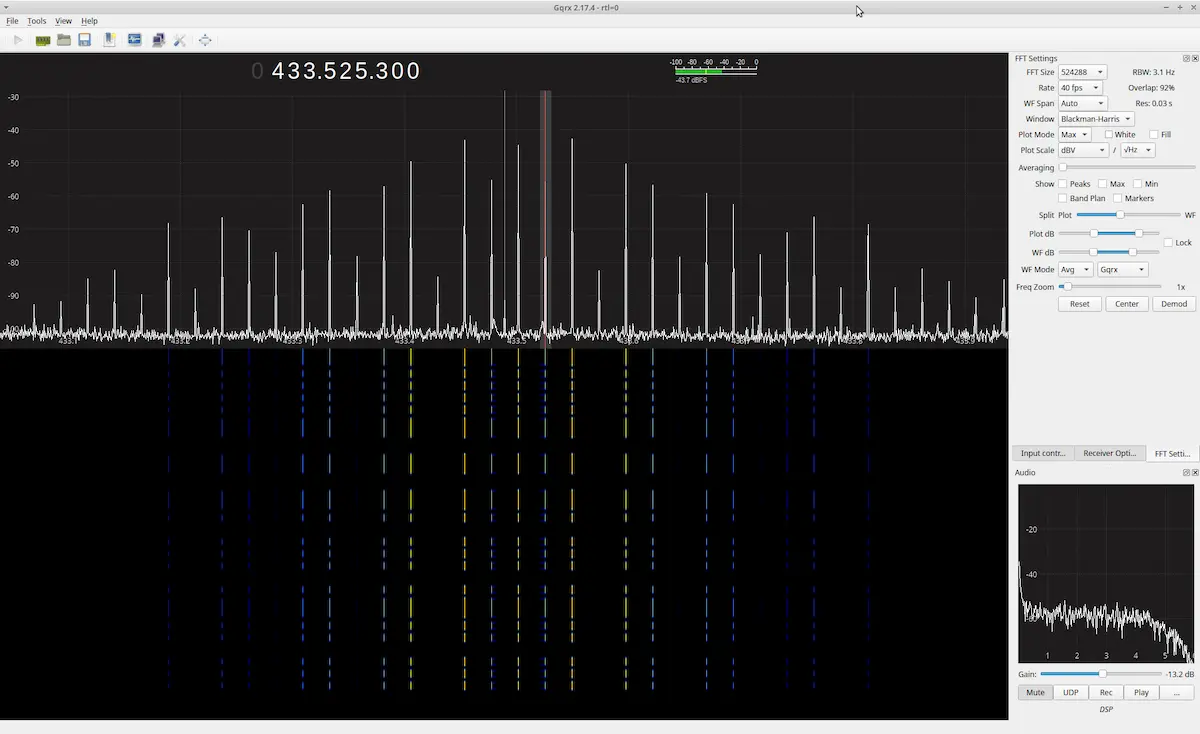
SATF-02 - Morse Code
The second satellite's signal was clearly Morse code, identifiable both in audio and in the waterfall display.
SATF-07 - Narrowband Audio File
The seventh satellite transmitted a narrowband FM audio file containing the flag. Anyone familiar with FM radio reception could recognize its spectral shape.
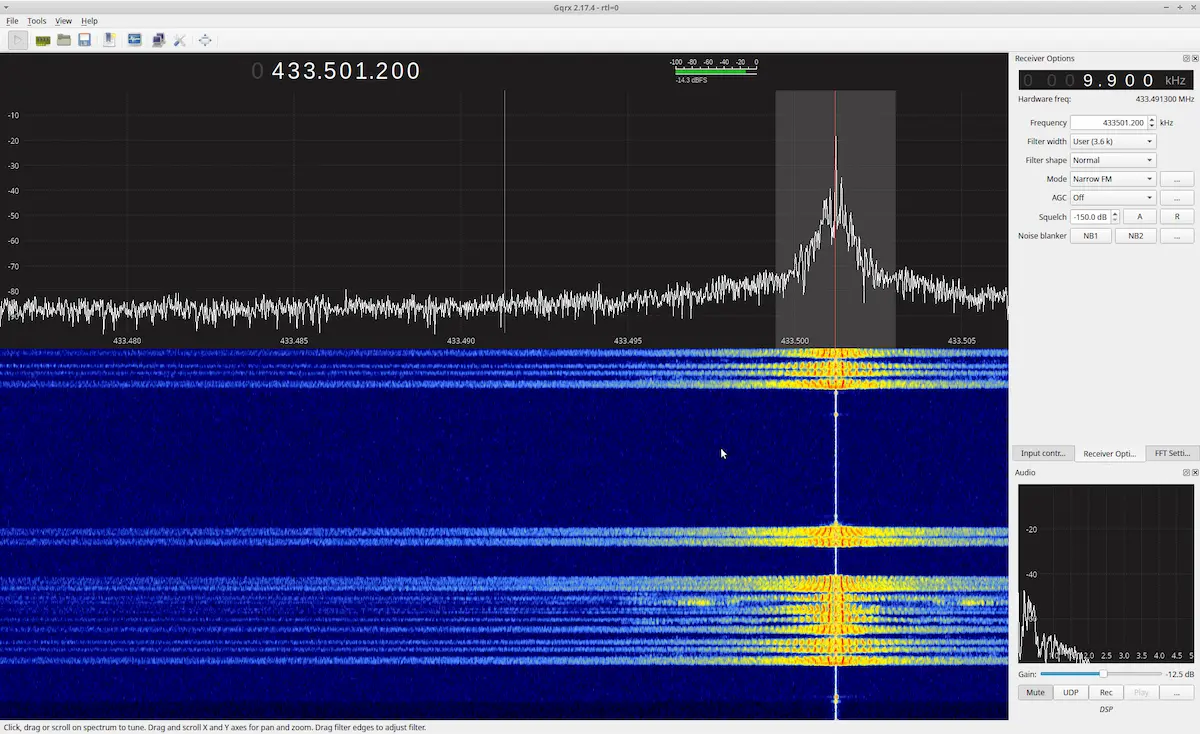
The remaining satellites used other modes and variations, each requiring a unique approach.
The Winner and Credits
A special prize was awarded on stage to the winner: Narken (Alluminati).
Special thanks to:
- Mikael Falkvidd - original challenge creator
- Jonathan B - for helping us with the setup of the challenge and a software refresh for Security Fest 2025
Interested in more?
Contact Assured Security Consultants for inspiring workshops and technical security training in your organization.
Browse our blog for more articles on security research, technical security best practice.
Read our publications for public penetration test reports, whitepapers, and more.
Explore our services in penetration testing, security engineering, advisory, and more.