2023 Retrospective: IT Infrastructure and Active Directory Security

The year of 2024 started with some high-profile attacks on business and government IT infrastructure, which received a lot of media attention. Our experience as technical cyber security specialists and as experts in offensive security is that Active Directory and network infrastructure is often an easy target for attackers mainly due to insecure configuration and not following industry best practices. Looking back on last year's engagements we will highlight why such attacks are often successful.
During the year of 2023, we at Assured Security Consultants conducted in-depth security assessments of IT infrastructure and Active Directory systems, uncovering a range of security vulnerabilities. Our objective in this blog post is to share these findings, providing a clear understanding of the common security issues we encountered. This is the first in a series of posts. In the next post we address our 2023 retrospective on Web and Mobile Application Security, and will ultimately cover the outcome of Automotive Security assessments conducted last year.
With this blog post and our continued work to help organizations secure their infrastructure, we aim to offer insights into the potential risks these vulnerabilities pose and discuss effective strategies for securing IT systems. This series will not only highlight the technical aspects of these security challenges but also address their implications for business operations.
Table of contents
- Summary of infrastructure and AD testing by Assured consultants in 2023
- Top 3 Issues 2023
- Common Issues
- Impact of New Regulations
- Conclusions
Summary of infrastructure and AD testing by Assured consultants in 2023
Last year, we conducted numerous penetration tests across a wide range of IT infrastructures and Active Directory systems. Our findings from these tests revealed a variety of security vulnerabilities, highlighting critical areas that organizations need to address.
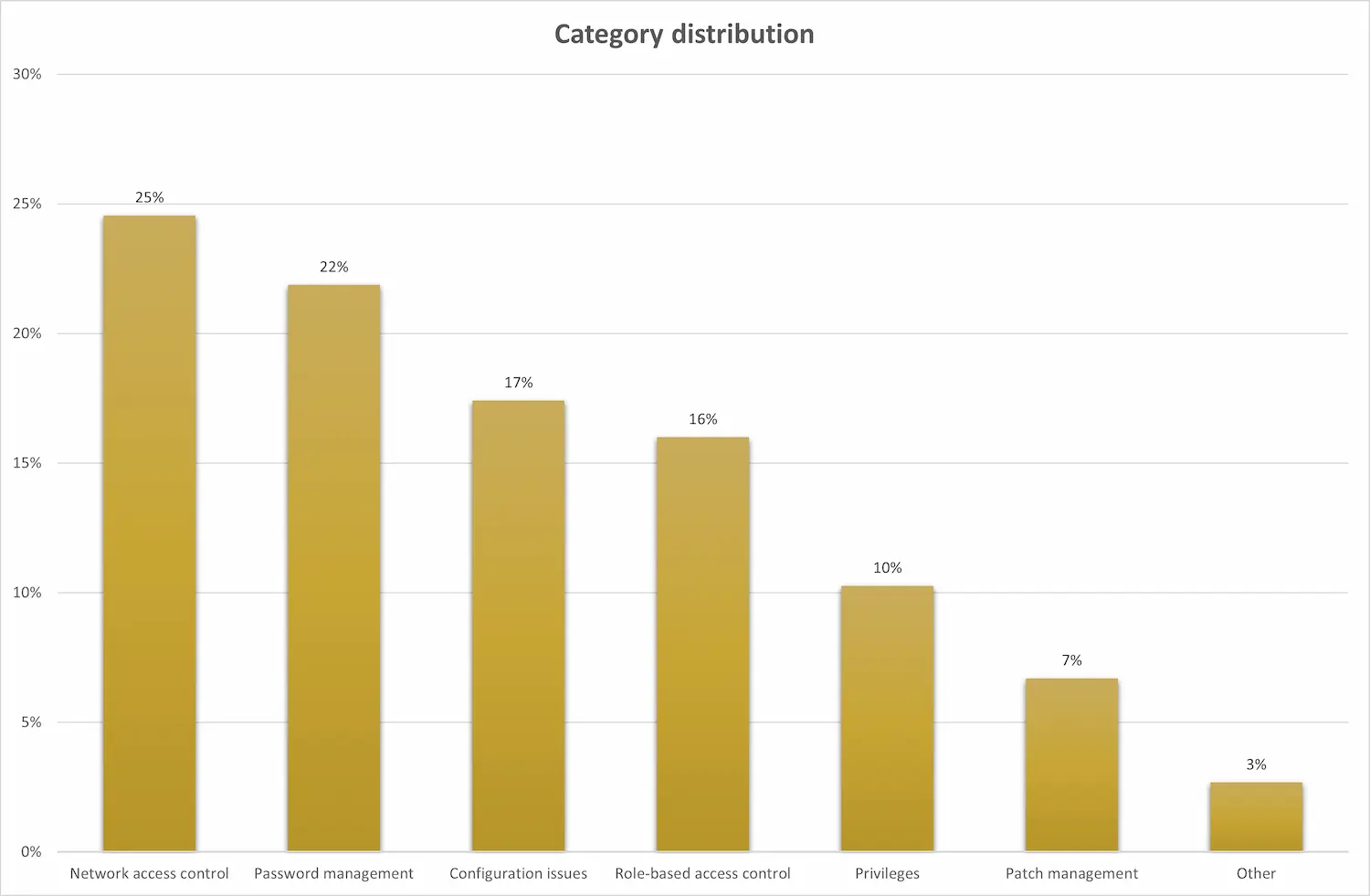
Issue Distribution Across Categories
Our analysis categorized each finding into distinct areas. We observed that certain categories were more prone to vulnerabilities than others, providing a clear picture of where organizations commonly fall short in their cybersecurity defenses.
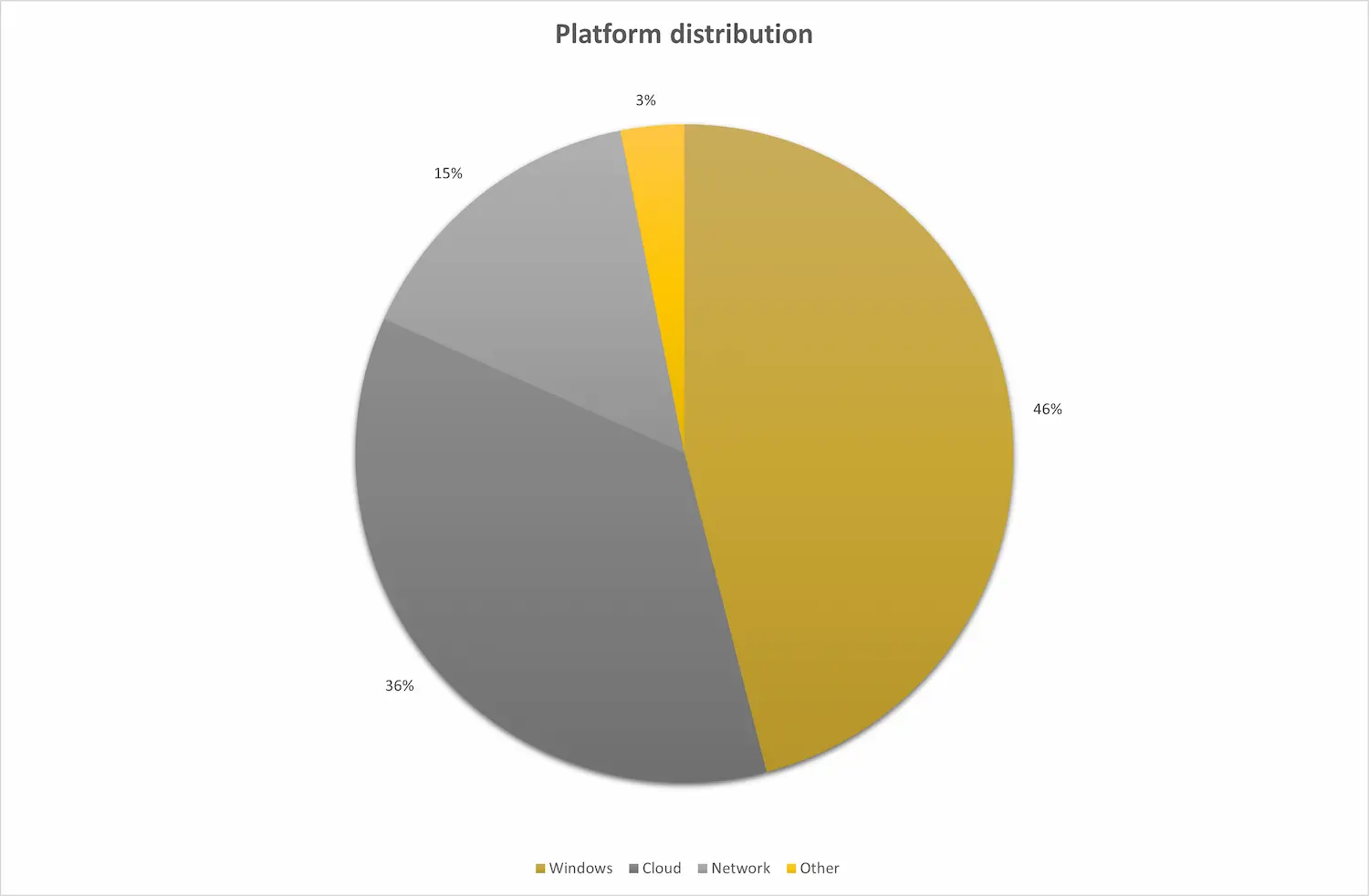
Platform Distribution of Identified Issues
We assessed various platforms including Windows, cloud environments (Amazon AWS, Microsoft Azure, and Google Cloud Platform), as well as network infrastructure. The data showed Windows as the predominant platform where most issues were identified, followed by cloud and network platforms. This distribution underscores the importance of focusing security efforts across diverse IT environments.
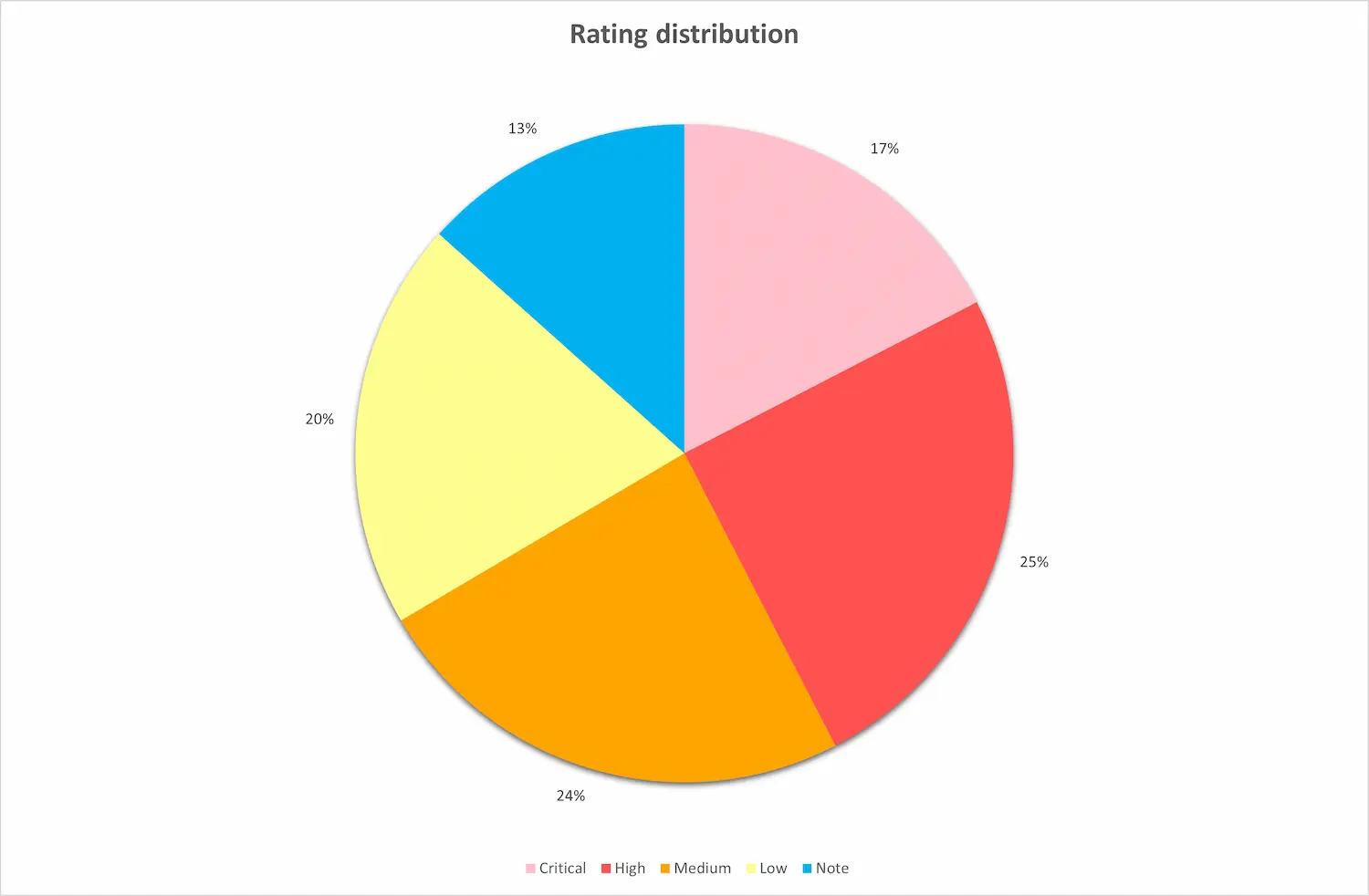
Severity of Identified Issues
In our assessments we rate the severity of each issue identified, classifying them into critical, high, medium, and low categories.
For infrastructure penetration tests we usually rate issues as critical or high where the vulnerability has a direct impact on the domain or a server that can give an attacker administrative privileges in the domain with no or few preconditions. Medium and low rated issues usually require further preconditions to exploit or have less impact to the domain, but can be often leveraged in combination with other issues to increase the impact.
Surprisingly, 17% of all our findings we rated critical and 25% were rated high. Most of these issues could allow an attacker to take control of a system or in some cases a whole domain or cloud tentant. Refer to the chart below for the full risk severity rating distribution.
Top 3 Issues 2023
In 2023, our penetration tests at Assured Security Consultants revealed some critical vulnerabilities that pose significant risks to IT infrastructure. Let's dive into the details of these vulnerabilities, their impacts, and our recommendations for mitigating them.
Weak Password Policy
Description: We often encountered domains with inadequate password policies. Windows domains typically allow the setting of a password policy that dictates the complexity and change frequency of user passwords. However, we found many instances where these policies were either default or too lenient, leading to easily guessable passwords.
Impact: Such weak password policies make systems vulnerable to password-based attacks, enabling attackers to perform lateral movement within the domain or escalate their privileges.
Recommendation: We strongly advise configuring the default password policy to comply with best practices from Microsoft. This includes a minimum password length of 14 characters and considerations for multi-factor authentication (MFA) and Local Administrator Password Solution (LAPS).
Further Reading: For more information, visit Microsoft's guidelines on password policy recommendations.
SMB and LDAP Protocols Vulnerable to Relay Attacks
Description: A significant number of systems were vulnerable due to unsigned SMB and LDAP network traffic. This vulnerability allows attackers to intercept authentication attempts and relay them, impersonating legitimate users.
Impact: These vulnerabilities expose systems to replay/relay and man-in-the-middle attacks, which can lead to unauthorized access to resources and data breaches.
Recommendation: Implementing mandatory SMB and LDAP signing via Group Policy is essential. This ensures that network traffic is authenticated and cannot be intercepted or altered.
Further Reading: Microsoft provides guidance on enabling SMB signing and LDAP signing, including LDAP binding and signing requirements.
ms-DS-MachineAccountQuota Not Set to 0
Description: The ms-DS-MachineAccountQuota attribute in Windows domains, by default, allows a user to create up to 10 machine accounts. We often found this setting unchanged, leaving a loophole for attackers.
Impact: Attackers can exploit this setting to create unauthorized machine accounts, leading to persistent access or privilege escalation within the domain.
Recommendation: Adjusting this attribute to 0 is crucial to prevent unauthorized machine account creation. This small change can significantly improve the security of your domain.
Further Reading: For more details, refer to Microsoft's documentation on machine account quotas.
Addressing these vulnerabilities is key to strengthening the security of your IT infrastructure. Implementing the recommended measures will significantly enhance your organization's cybersecurity resilience.
Common Issues
Our assessments throughout 2023 consistently highlighted several areas where security vulnerabilities were most prevalent. These common issues span various aspects of IT infrastructure, reflecting a need for comprehensive security strategies. Consistently across all platforms, we observe the majority of problems in the following areas:
- Network Access Control
- Password Management
- Configuration Issues
- Role-Based Access Control
- Privileges
Network Access Control
Network design often involves creating separate subnets for different types of devices, but a recurring issue was inadequate restrictions on access between these subnets. For instance, in some cases, clients' configurations allowed unrestricted connections between workstations and critical servers, increasing the risk of attacks.
To find a good solution for this, one must first consider what is reasonable. The example below demonstrates the difference between how an attacker connects to a system and how a user connects. In the example, the user connects to the Web server, which in turn connects to the Database server to deliver data back to the user. The attacker, on the other hand, connects directly to the Database server on MSSQL (TCP 1433). Attacks against the Database server on the MSSQL service could have been stopped by restricting who can connect to that server on that port. There is no scenario where a user should be able to connect directly to a database unless they are a database administrator.
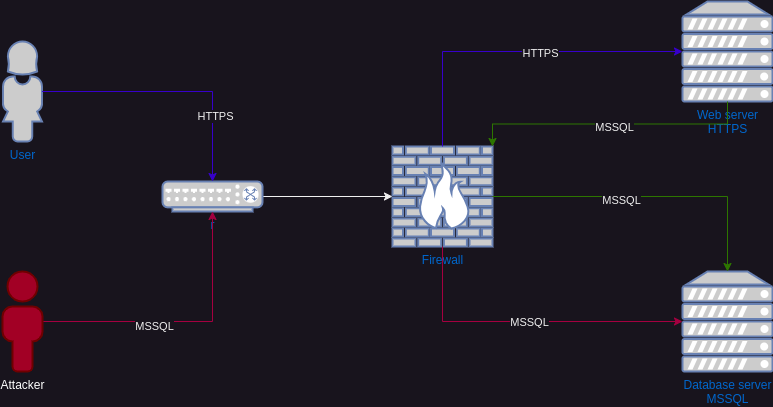
Something we often see is that clients (workstations) can connect to each other on various administrative services (e.g., WinRM on TCP 5985) or services like SMB. This also increases the attack surface for an attacker, which can be used for, e.g., lateral movement.
We recommend implementing strict access controls, ideally at the destination level. A practical approach includes grouping similar services in the same subnet and using host firewalls for fine-grained access control.
For example, web servers can be in one subnet, and databases in another. Clients can connect to web servers but not to databases. A rule to keep in mind is to have the strictest rules as close to the destination as possible and the least strict rules as close to the source as possible. Don't forget that in all common platforms today, there is a host firewall; here, too, you can configure rules to restrict access. This should be done in a centralized manner as it can easily become complex and challenging.
Password Management
Even in 2023, passwords remain a significant problem for our clients. This is also evident in reports from around the world, indicating that it is one of the most common reasons attackers gain access to an environment. This is not only a problem for users of the environment, but we also see system administrators not following password policies or reusing passwords between systems.
In Sweden, users still create passwords like Sommar2023!, Vinter2020, and Password123. It has long been known that users will choose the easiest path when creating their passwords. The IT department establishes a technical password policy based on decisions from leadership, such as requiring 10 characters, a digit, and a special character. In such cases, a password like Sommar2023! meets the criteria. Or, let's increase the password length to 14 characters, and we get Varmsommar2023!. Weak passwords are challenging to address in an organization where hundreds of users need to log in to their workstations every day. When we discover weak passwords at a client, we usually provide the following recommendations:
- Password length of at least 14 characters
- Do not force password changes more frequently than once a year (365 days)
- Prohibit common words in passwords, such as
Sommar - Implement a lockout policy
- Consider a solution for multi-factor authentication (MFA)
- Implement LAPS (Local Administrator Password Solution)
A good MFA solution for managing a Windows Active Directory environment is Windows Hello for Business. It effectively eliminates the use of passwords, addressing the issues of weak passwords and password reuse (when using Hello for Business). It can also be an effective defense against phishing attacks.
Another option is to implement a password manager for users, especially for system administrators who need to manage secrets for multiple systems, network equipment, service accounts, etc. Various password managers, such as Keepass, 1Password, Bitwarden, offer different solutions. Evaluate which password manager best suits your organization. Meanwhile, encourage your system administrators to download KeePass (or equal) to at least protect administrative account passwords.
We often find passwords (in plaintext) for accounts or systems written in documents and configuration files on file shares. While these passwords are often longer and more complex, their presence in plaintext diminishes their significance. Therefore, using a secret manager for applications and systems needing secrets at runtime is crucial. An example of this is Hashicorp Vault.
We also frequently encounter weak passwords on service accounts in an environment. In Windows Active Directory, there are built-in features to protect service accounts, such as standalone managed service accounts (sMSA) and group managed service accounts (gMSA). These features facilitate password management for service accounts in a Windows environment.
When the new password policy is in place, we recommend reviewing old passwords, especially important for accounts that do not need to change passwords in the environment, and ensuring that they comply with the new password policy. Also, make sure there are no reused passwords or passwords in plain text in scripts or configuration files.
In Windows environments, we don't just guess passwords or find them in text documents during our penetration tests. We can also retrieve them directly from the system memory. These attacks have been utilized for a very long time with tools such as Mimikatz to help an attacker achive this. Microsoft has implemented a good solution to mitigate these attacks called Credential Guard which is enabled by default starting from Windows 11, version 22H2. Credential guard protects NTLM hashes, Kerberos Ticket Granting Tickets (TGT) and application stored credentials by keeping the secrets in a virtualized secure vault.
Configuration Issues
Misconfigurations in services were another common finding. For example, the default setting of the ms-DS-MachineAccountQuota attribute in Active Directory can be exploited for privilege escalation or persistence in the environment.
Many services are delivered in a default mode where the configuration is based on the service's basic functionality. Adding security to the service is usually available, but as an administrator, you must configure the service yourself to make it secure. The problem with services delivered without security as the default is that the administrator must be aware of all the different configuration attributes that need to be changed to enhance the security level of the service, which is not always easy. It often happens that an administrator also makes configuration changes to a service that opens up security vulnerabilities. We also want to make it clear that several other categories described in this article may stem from configuration issues.
Just like real threat actors do, we exploit configuration errors to achieve our goals. To provide good examples of this, there is an attribute in Windows Active Directory called ms-DS-MachineAccountQuota. This attribute specifies the number of computer accounts a domain user can create in the domain and is set to 10 by default. We have seen cases where customers have set the attribute to 0 (which is recommended), and we have seen cases where customers set it to > 10 (actively increasing the value). Being able to create computer accounts in a domain can be exploited by an attacker for various purposes, such as establishing persistence in the environment or as a prerequisite to elevate their privileges abusing Resource Based Contrained Delegation (RBCD). RBCD can be abused when an attacker have control of a user account in the domain with write privileges to a victim computer account, and have created (or in other ways have access to) a computer account with a Service Principal Name which by default any domain user can do (because of the ms-DS-MachineAccountQuota attribute). The attacker can then set the attribute ms-DS-Allowed-To-Act-On-Behalf-Of-Other-Identity on the victim computer account to the controlled computer account the attacker created. The attackers computer account can now impersonate user or computers with access to the victim computer.
Another common scenario we encounter involves the lack of signing in SMB or LDAP. SMB Signing is enabled by default on Domain Controllers but no other servers, LDAP signing is not enabled by default even on Domain Controllers. Without signing enabled these protocols do not authenticate the sender, creating an opportunity for attackers to execute relay attacks on SMB or LDAP. A relay attack occurs when an attacker captures authentication packets for an account and then forward them slighly modified to another system which do not require signing. If the target system does not mandate a signature, it is unable to ascertain the origin of the packets and the attacker could authenticate against the system as the original account, performing any actions the original account could perform on the system.
The last configuration issue we want to address are Kerberoasting. By default in a Windows domain all service accounts having a Service Principal Name (SPN) set. A SPN is a unique identifier used to associate a domain account with a service and a host. For example MSSQL/db.example.com. An attacker can make a request to the Domain Controller to obtain a service ticket for the service, where parts of the service ticket is encrypted using the domain account (service accounts) password. An attacker can then perform an offline brute force attack to obtain the password for the service account. By default, modern Windows domains uses AES256 when encrypting the service tickets, but an attacker could specifically request the service ticket to be encrypted with RC4 (if it is supported) to improve the speed for offline brute force attacks since RC4 is a weaker algorithm than AES256.
There are so many different attributes in Windows, Linux, Cloud, and network products to configure that it is impossible for us to granularly cover even a fraction of them. Therefore, we want to provide some general advice that can be used for already installed services or new services to be installed in your environment.
- Read the manual. What is the default configuration? What is recommended by the provider?
- Test the configuration. What other services, users, systems are affected by the change?
- Document the configuration change.
Regular audits and adherence to security best practices for service configurations are essential. Resources like Microsoft’s guidelines for SMB signing and LDAP signing/binding can be invaluable for administrators.
To protect against Kerberoasting attacks the most important mitigation is to create strong passwords for your service accounts, and to put all service accounts in the Protected Users Group which also disables RC4 support (see Password Management section).
Role-Based Access Control
With Role-Based Access Control, we mean limiting access to information and data. We often see that users have access to more information and data than they need to perform their work. This is a difficult nut to crack and plagues many system administrators daily.
During our tests, we often delve into the deep hole of file servers. There, both users and administrators store all kinds of information that can be very helpful for an attacker during an ongoing attack. We often find passwords, backups, sensitive documents, and personal information, to name a few things. We then use this in our tests for privilege escalation and lateral movement.
The most common thing we see is that a user in the environment has read rights to many more file shares than necessary. Many times, the user also has write rights, opening up a range of new possibilities for an attacker. An attacker who can write over files can make information unreliable or even harmful. For ransomware actors, write rights are important as they want to overwrite existing files with an encrypted version of the files.
But it's not just file servers that users have access to. Even services and systems can sometimes be accessible to a user who doesn't need them. For example, we have encountered situations where groups like Authenticated Users or Domain Users have mistakenly been given privileges to connect with Remote Desktop Protocol (RDP) and log in to servers, or have privileges to retrieve authentication certificates for other users by abusing vulnerable certificate templates in Active Directory Certificate Services (ADCS).
Vulnerable ADCS templates are something we have abused in several penetration tests. To get a good understanding about the different attack techniques against ADCS and mitigations see this great whitepaper from Specterops called Certified Pre-Owned. We often identify certificate templates in ADCS with the flag ENROLLEE_SUPPLIES_SUBJECT set and the template permits for example the Domain Users group to enroll. Any member of the Domain Users group can retrieve a certificate for any other user in the domain.
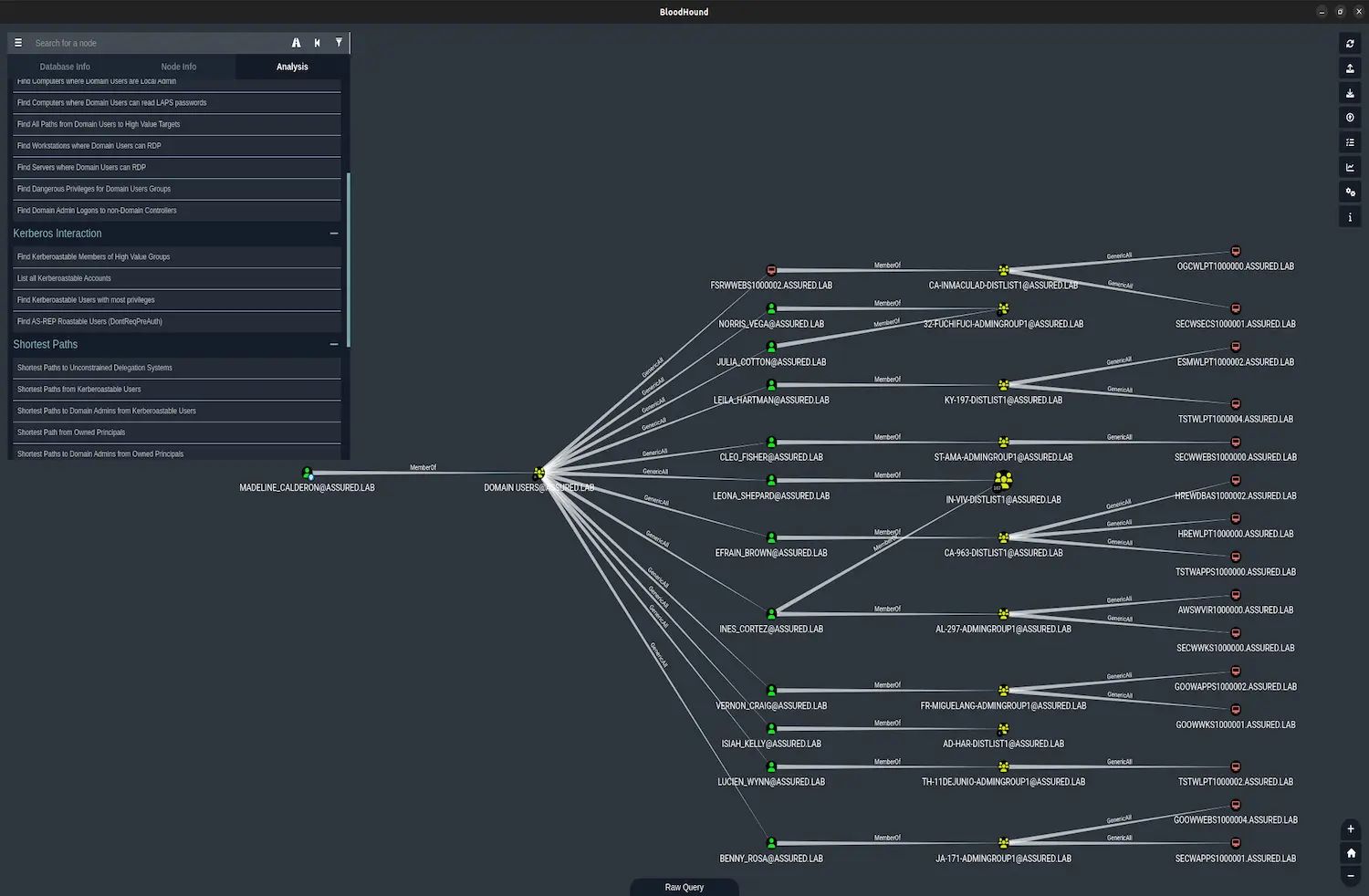
There is no way to ensure that everyone has access only to what they need all the time, even if there are vendors who claim otherwise, but there are ways to continuously work to effectively reduce the risk of these types of problems arising. For a Windows Active Directory environment (or Azure, for that matter), there is a fantastic tool that we use in our tests called Bloodhound. Bloodhound collects information about all objects in Active Directory or Entra ID (formerly Azure AD) and creates a graph database (Neo4j). Through a web interface or a client interface, you can query the database and get the result in a graph (see the image below).
To identify file shares and their users' privileges there is a tool from NetSPI called PowerHuntShares. With PowerHuntShares, you get a clear report on which file shares exist and what rights the user has to them. It is important to note that the result from the context from the user running the program and does not provide a complete picture of the current situation. Still, it can give a quick and clear picture from one perspective.
The most important thing is to have a clear process for identifying and managing permissions in the environment. A good process to follow is:
- Identify systems and file shares.
- Document current privileges (share ACL, file rights, or system permissions).
- Document required privileges (share ACL, file rights, or system permissions).
- Configure the privileges to meet the requirements.
- Test.
Privileges
We frequently encountered identities, including service accounts, with higher privileges than necessary. This over-privileging can be exploited by attackers to gain unauthorized access to critical systems.
Sometimes it is difficult to keep track of the privileges an account needs; many times, it is well-documented for the service or program you are going to install. But sometimes there may be unclear instructions on what to do. Here too, Bloodhound can be very helpful in a Windows environment.
Microsoft has a good article describing how to manage administrative accounts to try to achieve a least privilege model. Least privilege means that, as a rule, an account should have as few privileges as possible, precisely those needed to perform a specific task. This is a difficult and challenging rule to follow, but there are several methods you can use to come close to the least privilege model.
When an administrator needs higher privileges, the administrator should only get it for the task they are going to perform. To achieve that, you can limit from where an administrator connects to reduce exposure of administrator credentials. This can be done through Privileged Access Management (PAM). PAM is a strategy to set up an administrative environment that is controlled, hardened, and monitored. Similar solutions are also available for AWS, GCP, and Azure.
Impact of New Regulations
The evolving regulations NIS2 and EU CRA pose examples of new security challenges for organizations managing infrastructure. These directives have significantly influenced how organizations approach cybersecurity, embedding it as an integral part of their operational fabric. Compliance with these regulations is no longer optional but a crucial aspect of business strategy, especially for those handling sensitive data or critical infrastructure.
These new regulations emphasize the need for organizations to not only react to cybersecurity incidents but also proactively implement measures to prevent them. This shift towards a proactive cybersecurity stance involves regular assessments, timely patch management, and continuous monitoring of the IT environment.
Conclusions
Our data shows that most of our findings are related to issues that have been common almost since the beginning of IT. Organizations still have a hard time managing the complexity of their environments with servers, identities, passwords, etc. Combined with all these services the digitalization needs to function and deliver value to users which adds even more complexity.
Complexity makes even the simplest solutions harder to implement and leaves the organization vulnerable to quite simple attack techniques. Most threat actors don't use flashy 0-days to breach organizations, they send phishing emails when employees are stressed, they use vulnerabilites dated several years back or find services with default passwords configured. Threat actors don't use advanced techniques, they use what works.
The most common issues we identify are all relatively simple for an attacker to exploit or abuse. Password Guessing (T1110.001 Brute Force: Password Guessing) is a technique commonly used to find valid credentials and with weak or default passwords the probability for a successful attack increases.
Once an threat actor get access to the corporate network SMB and LDAP relay (T1557.001 Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay) can be used to steal more credentials in the domain, and possibly increase privileges.
To get persistence in the domain and to make it harder for the organization to stop an attacker could abuse the MachineAccountQuota to create a computer account in the domain (T1136.002 Create Account: Domain Account).
New (or revised) directives and regulations such as NIS2 and EU CRA are coming in hot forcing more and more businesses to work with IT and information security as an integrated part of their organization. These regulations also hold the board accountable if the requirements is not met, which make it more likely that IT security is added as a priority at the board level.
We strongly recommend all organizations with digital assets, big or small, to prioritize work with proactive security. Make sure you have a good understanding on all your assets, you can't defend what you don't know. Increase awareness in your staff, have them take small trainings to understand not only how to identify phishing emails but also why they need to. What are your employees part in all of this, what can they do and why should they.
A good way to start is to do an infrastructure penetration test, which will identify not only assets but also issues which could be abused to harm those assets. The result from the penetration test is a structured and detailed report on all identified issues risk-rated from critical to low to help prioritizing which issues to deal with first, recommendations for how to mitigate each issue and an executive summary to describe the actual business impact an attack could have on the organization.
The increasing emphasis on cybersecurity regulations is a positive step towards integrating robust security practices into every aspect of digital operations. As cybersecurity consultants, we at Assured Security Consultants are committed to helping organizations navigate these challenges.
Our team of senior security experts brings years of experience in network and infrastructure penetration testing, both on-premise and in the cloud, and we are well-equipped to provide comprehensive support, from advisory services to Red Teaming activities.
If you have any questions or if you are interested in our services, don't hesitate to contact us!